Which Internet Fraud Involves Using Social Engineering Techniques
CEO fraud business email compromise and whaling are specific forms of impersonation attacks where malicious individuals pose as high-level executives within a company. This type of attack targets businesses and frequently involves criminals using social engineering or computer intrusion techniques to compromise legitimate business email accounts to conduct unauthorized transfers of funds.
Understanding Social Engineering Techniques
Phishing What keeps unauthorized Internet users out of private intranets.

. Using this technique the social engineer may lure the user with promises of making a lot of money online by filling in a form and confirm their details using credit card details etc. Exploiting human greed. Social engineering attacks come in many different forms and can be performed anywhere where human interaction is involved.
A sophisticated scam targeting businesses working with foreign suppliers and companies that regularly perform wire transfer payments. As its name implies baiting attacks use a false promise to pique a victims greed or. Social engineering attack techniques.
Gmail or Hotmail. What is easily observable is that social engineering gained strength from the 2000s onwards following the computer and the internet boom in the 1990s. A type of social engineering technique used to obtain information such as personal identification numbers PINs passwords and other confidential data by looking over the victims shoulder either from keystrokes on a device or sensitive information being spoken and heard also known as eavesdropping.
What keeps unauthorized Internet users out of private intranets. Which internet fraud involves using social engineering techniques. Criminal actors primarily conduct SIM swap schemes using social engineering insider threat or phishing techniques.
Impersonation attacks are typically malware-less attacks conducted through email using social engineering to gain the trust of a targeted employee. A pretext is a false motive. Which Internet Fraud Involves Using Social Engineering Techniques.
As of the early 2000s another type of social engineering technique includes spoofing or hacking IDs of people having popular e-mail IDs such as Yahoo. Which Internet fraud involves using social engineering techniques and attempts to deceptively gain private information by masquerading as a legitimate business organization. What kind of hardware does a firewall use.
Stingy with your info Check financials often ASK for credit report. Pretexting is a form of social engineering in which an individual lies to obtain privileged data. Telephone banking fraud involves criminals calling up bank customers and asking for their username and passwords.
Privacy What is a criminal activity that involves using social engineering techniques and attempts to deceptively gain private information like usernames PIN numbers passwords and credit card details by masquerading as a legitimate business organization. What Security Threat Is Social Engineering. They may for example use social engineering techniques as part of an IT fraud.
The following are the five most common forms of digital social engineering assaults. What Skills Do You Need To Become A Cybersecurity Specialist. SIM swapping is a malicious technique where criminal actors target mobile carriers to gain access to victims bank accounts virtual currency accounts and other sensitive information.
There are several types of social engineering including telephone banking fraud spoofed emails and web browser malware. Many of those complaints involved some form of social engineering. Why Cybercrime Is Increasing.
Despite the difficulty we created a triple listThese are three real cases of attacks that trace back to the origins and use of social engineering in the age of computers and the Internet. Business E-Mail Compromise BEC. This is probably the most well-known technique used by cybercriminals.
What is the abuse of an email system called. Your work laptop may not be as secure as it should be. Phishing attacks non-payment or non-delivery ploys and extortion scams were the most prevalent types of ruses with romance and.
How a SIM Swap Scheme Works. Lets look at some of the most common social engineering techniques.

Social Engineering How Hackers Get At Your Date

Social Engineering Attacks Prevention And Best Practices Loginradius Loginradius Blog

Social Engineering Attacks Download Scientific Diagram
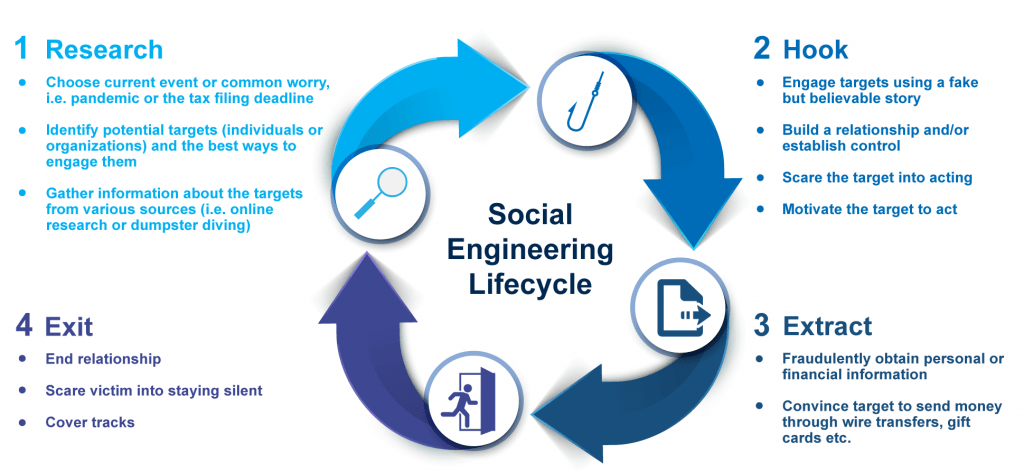
Social Engineering What It Is And How To Prevent It Bsg Blog

Social Engineer Gw Information Security Blog

What Is Social Engineering Definition Types Techniques Of Attacks Impact And Trends Toolbox It Security
Social Engineering What It Is And How To Prevent It Bsg Blog

Tailgating Social Engineering Attacks

1 Phases Of The Social Engineering Defensive Framework Download Scientific Diagram

15 Social Engineering Examples Real Attacks Updated 2022 Tessian

Social Engineering What It Is And How To Prevent It Bsg Blog

Pdf Social Engineering Attack Framework

What Is Social Engineering And How Can You Avoid It

5 Social Engineering Attacks To Watch Out For The State Of Security

Social Engineering Attacks A Look At Social Engineering Examples In Action Hashed Out By The Ssl Store

Social Engineering Attacks A Look At Social Engineering Examples In Action Hashed Out By The Ssl Store

What Is Social Engineering 4 Types Of Attacks Tessian

What Is Social Engineering Examples Prevention Tips Managed It Services And Cyber Security Services Company Teceze
Comments
Post a Comment